

Advanced deployment and troubleshooting
A song of ISE and Posture:
BRKSEC-3077
Andrea Bertorello, Security Consulting Engineer

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
About me
BRKSEC-3077
• AAA TAC Engineer
• ThousandEyes Support Engineer
• Security Consulting Engineer
Warning!
Italian accent ahead
4

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Icon Used Through the Presentation
BRKSEC-3077
Hidden Content – slides which won’t be presented durith the
session. Those slides are here to give you later more context
and detailed information
Waring – Extra attention during the configuration
Content enlarging – when something is not visible good enough we
highlight and enlarge this area.
GUI navigation assistant – This special type of highlighting is used to
help you in navigation in the Graphical User Interface of a product.
1
For your Reference – these items could not be covered in detail
during the session.
5

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Basic Posture
• ISE Posture 101
• ISE Posture Journey
Advanced Scenarios Application
• Posture, MFA, VPN and Duo Proxy
• Posture, MFA, Duo DAG and ASA with
SAML
Advanced Posture
Processes
• Session Sharing
• Discovery Process
• Compliant State
Posture
Troubleshooting
• Deep Dive
Troubleshooting
• Learn on Example
Agenda
BRKSEC-3077
7

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Session Objectives
BRKSEC-3077
Session will cover:
• Theory of Posture
• Posture deployment scenarios
• Troubleshoot methodology
Session will not cover:
• Marketing
• Roadmaps
• All possible ISE posture features
8

Posture 101

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Posture from 10000 feet
AnyConnect
Policy Enforcement
Decision Making
Endpoints/Agents
Foundation
Admin
Posture Updates
Remediation Servers
ISE
ISE
BRKSEC-3077
11

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Posture Lifecycle
BRKSEC-3077
Step 1 Step 2
Step 3 Step 4 Step 5 Step 6
Step 1
Step 2
Step 3 Step 4 Step 5Step 0 Step 6
Authentication
Client
Provisioning
Posture
Time
Remediation
CoA
Final
Authenticatio
n
ISE
Remediation Servers
Manual
Installation
12

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Posture Flow types
BRKSEC-3077
Redirect based Non-redirect based
13

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Posture with pre-installed Agent (no-profile)
BRKSEC-3077
ISE
ISEPostureCFG.xml
HASH=123
ISEPostureCFG.xml HASH=321
Overwrite
ISEPostureCFG.xml
HASH=321
21

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco PublicBRKSEC-3077
Posture with pre-installed Agent (no-profile)
For every primary record
you have a <time> tag
ConnectionData.xml file
created on the first
posture attempt
ConnectionData.xml
Every next server is added
as a separate Primary
record
22

ISE Posture
Journey

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Posture Journey
BRKSEC-3077
Posture Updates
Global Settings
Client Provisioning
Posture
Policies
Access Policy
Go Live
29

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Posture Journey: Posture Updates
BRKSEC-3077
Posture Updates
30

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Posture Updates
BRKSEC-3077
ISE
Proxy Settings
Posture Updates
Deleted default posture elements are not created again during next updates
31

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Posture Journey: Global Settings
BRKSEC-3077
Posture Updates
Global Settings
33

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Global Settings
BRKSEC-3077
What if client does
not support
posture?
Time for the user
to remediate
Global Settings
34

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Global Settings
BRKSEC-3077
Posture Lease
Agentless Plugin
Cisco ISE will use the last
known posture state and will
not reach out to the endpoint
to check for compliance.
Global Settings
35

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Posture Journey: Client Provisioning
BRKSEC-3077
Posture Updates
Global Settings
Client Provisioning
37

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Posture: Agent types
BRKSEC-3077
AnyConnect
AnyConnect Stealth
Temporal Agent
Agentless
ISE
Client Provisioning
38

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Which agent you need ?
BRKSEC-3077
AnyConnect
AC Stealth
Temporal
Agent
Agentless
Visibility
Time to
implement
More
Protection
Specific
Capability
OS, Remediation, Reassessment, Checks
Client Provisioning
47

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Client Provisioning
BRKSEC-3077
Some agents must be
downloaded from Cisco
Software Center and
uploaded manually
Resources
AnyConnect Profile
Client Provisioning Policy
Client Provisioning
49

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Client Provisioning: What is compliance module
BRKSEC-3077
Client Provisioning
Compliance Module - Offers the ability to assess an endpoint’s
compliance.
OPSWAT - Cisco Compliance module is using OESIS framework
from OPSWAT for detection and remediation
https://www.slideshare.net/OPSWAT/introd
uction-to-oesis-framework
50

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Let’s visualize
Client Provisioning
New AV
Released
New AV
Info
New OESIS
Version
New Compliance
Module
Cisco Cloud
Posture Updates
New AV
Info
New AV
Info
Define posture policy:
Requirements -
Symantec X INSTALLED
AND
Symantec X UP_TO_DATE
BRKSEC-3077
51

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Let’s visualize
Client Provisioning
Cisco Cloud
Posture Updates
Symantec X INSTALLED?
Symantec X UP+TO_DATE
Compliance Module
BRKSEC-3077
52

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Compliance module updates vs Posture updates
BRKSEC-3077
Client Provisioning
Posture Updates
On ISE
Compliance Module
DB Application
Actions
Corresponding
Posture Policy
ISE
53

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Client Provisioning
BRKSEC-3077
Resources
AnyConnect Profile
Client Provisioning Policy
Client Provisioning
54

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Client Provisioning
BRKSEC-3077
Client Provisioning
55

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Client Provisioning
BRKSEC-3077
Resources
AnyConnect Profile
Client Provisioning Policy
Client Provisioning
56

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Client Provisioning
BRKSEC-3077
Resources
AnyConnect Profile
Client Provisioning Policy
Client Provisioning
Configuration Name
Compliance Module
Modules
Profile AC
In case of posture over VPN AC cannot be
updated if ISE has higher AC pkg version then
ASA
57

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Client Provisioning
BRKSEC-3077
Resources
AnyConnect Profile
Client Provisioning Policy
Client Provisioning
Specify the
AnyConnect
Agent
Configuration
58

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Posture Journey: Configuration
BRKSEC-3077
Posture Updates
Global Settings
Client Provisioning
Posture Policies
60

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Posture Checks
BRKSEC-3077
Conditions
ISE
Remediation
Anti-Malware
Anti-Spyware
Anti-Virus
Application
Compound
Dictionary Compound
Dictionary Simple
Disk Encryption
External DataSource
File
Firewall
Hardware Attributes
Patch Management
Registry
Script
Service
USB
Condition + Remediation Requirement
Posture Policies
61

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Posture Policy
BRKSEC-3077
Policy Elements Policy Sets
Posture Policies
62

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco PublicBRKSEC-3077
Posture Script Condition
[ … ]
Are all corporate CA certs and
no rogue CA certs installed ?
Has the user over-written
network configuration to
use specific DNS ?
.ps1
.sh
ISE
Script Push
Response
Dynamic requirements
Posture Policies
New
63

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco PublicBRKSEC-3077
Posture Script Condition – Prerequisites
Establish trust
ISE
AnyConnectLocalPolicy.xml
SHA-256
PSN
Local Machine Store
Posture Policies
New
64

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco PublicBRKSEC-3077
Posture script condition – Script Dowload
ISE
.ps1
.sh
%LOCALAPPDATA%\Cisco\Cisco
Anyconnect Secure Mobility Client\scripts
~/.cisco/iseposture/scripts
%ALLUSERPROFILE%\Cisco\Cisco
Anyconnect Secure Mobility Client\ISE
Posture\scripts
/opt/cisco/anyconnect/iseposture/scripts
Elevated privileges
Filename match
Script file hash
match
Reuse the
existing script
Download the
script
Posture Policies
New
67

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco PublicBRKSEC-3077
Posture script condition – Exit Code
ISE
Exit code
<0 : pre-defined exit code
>0 : user-defined exit code
Posture Policies
Other failure possibilities:
Script exit code must be
between 0 and 255
68

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Posture Journey: Access Policy
BRKSEC-3077
Posture Updates
Global Settings
Client Provisioning
Posture
Policies
Access Policy
71

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Access Policies – Redirect Chaining
BRKSEC-3077
We need to redirect our clients to the Client Provisioning Portal, provide
access or deny it.
Must exists on NAD
Access Policy
NonCompliant
Compliant
Unknown
72

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Posture Journey: Time to Go Live
BRKSEC-3077
Posture Updates
Global Settings
Client Provisioning
Posture
Policies
Access Policy
Go Live
73

Advanced
Posture
Processes

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Session Sharing
“Session context is shared within ISE deployment so
PSN can run posture even when authentication hit
another node”
ISE
Node Group
Light Session Directory
BRKSEC-3077
76

Is session context shared
within ISE deployment ?
ⓘ Start presenting to display the poll results on this slide.

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Session management - theory walkthrough
Who is responsible for session management in ISE deployment?
Syslog - Authentication Passed
Syslog - Accounting Start
Syslog - Accounting Stop
Syslog - Accounting Update
BRKSEC-3077
MNT
PSN
Sessions are created:
Sessions are updated:
78

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Session management - theory walkthrough
Who is responsible for session management in ISE deployment?
Access-Accept
Accounting Update
Accounting Start
Accounting Update
BRKSEC-3077
PSN
Sessions are created
Sessions are updated
80

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
PSN
Node Group
82
BRKSEC-3077
Main idea behind is to minimize amount of global replication events
Session-ID Session-Attributes
ABC {alice,MAC,IP, redirect-url=psn1}
Session-ID ABC
Status – Started
redirect-url=psn1
SW#sh authentication
sessions interface
g1/0/5 details
…
url-redirect=psn1
Node Group members
monitor each other
In case of outage all
sessions in redirect
state are downloaded
from MNT
COA
Terminate
PSN session
chance
PSN
MNT
Live
Sessions

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Light session directory (LSD) AKA Light Data
Distribution (LDD)
BRKSEC-3077
RabbitMQ
Channel
Session-ID ABC
Attributes{alice,MAC,IP,}
Limited list of
attributes added
to LSD
Session-ID ABC
Initial authentication
Accounting Interim update
with Device Sensor Info
PSN
PSN
PSN Session Cache
PSN Session Cache
LSD Cache
83

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
How Light Data Distribution (LDD) solve posture
problems
BRKSEC-3077
PSN1
PSN2
LSD Cache
RabbitMQ
Cache Entries
ABC {LSD attributes +
Posture Status}
Cache Entries
ABC {LSD attributes +
Posture Status}
Initial authentication
Posture Check
COA/Final
authentication
Re-authentication
ISE
ISE
ISE
LSD Cache
RabbitMQ
85

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
How Light Data Distribution (LDD) solve posture
problems
BRKSEC-3077
PSN1
PSN2
PSN session chance
PSN session chance
LSD cache
LSD cache
RabbitMQ
Channel
Session-ID ABC
Attributes{alice,MAC,IP,}
Attributes added to
LSD
Session-ID ABC
Authentication
Session-ID BCD
Attributes{alice,MAC,IP,}
Discovery request
Session lookup
Check is there is a
newer session in LDD
ISE
ISE
86

Demo – Node Group
and Phantom Session

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco PublicBRKSEC-3077
92

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Posture Status Sharing over RSD – PSN Failover
BRKSEC-3077
1. Authentication happens on PSN-1, authorization profile with redirection
is assigned.
2. COA after successful posture assessment.
3. Next authentication when authorization profile for the compliant state is
assigned.
4. Authentication hits different PSN but it still gets authorization profile for
the compliant state.
ISE-PSN1
ISE-PSN2
101

Demo RSD

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Insert Video DEMO RSD

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Posture Discovery and Authentication
BRKSEC-3077
”Every time when dot1x authentication happens,
Discovery process is restarted by the ISE posture
module”
106

Every time when dot1x authentication
happens, Discovery process is restarted
by the ISE posture module
ⓘ Start presenting to display the poll results on this slide.

Demo – Identification

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Insert DEMO Discovery

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Discovery
BRKSEC-3077
ISE
ISE
Power Events User Login
Initial AC
Installation
Return
sleep
Default GW
change
Interface
Up
alice
*****
110

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
PSN discovery Redirect flow
Network Access Device
Stage 1 Discovery
One Stage
1 cycle is
limited to 5
seconds
HTTP Get to Discovery Host (IF available)
HTTP Get to enroll.cisco.com
HTTP Get to Default GW IP
HTTPS request to PSN
Find My Session {IP Array}, {MAC Array},
Session
lookup in
Local PSN
cache
(IP/MAC
based)
Session
lookup on
MNT cache
(MAC only)
ISE
PSN
BRKSEC-3077
112

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
PSN discovery Redirect flow
Network Access Device
Stage 1 Discovery
One Stage
1 cycle is
limited to 5
seconds
HTTP Get to Discovery Host (IF available)
HTTP Get to enroll.cisco.com
HTTP Get to Default GW IP
HTTPS request to PSN
Find My Session {IP Array}, {MAC Array},
Session
lookup in
Local PSN
cache
(IP/MAC
based)
Session
lookup on
MNT cache
(MAC only)
ISE
PSN

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
PSN discovery Redirect flow
Network Access Device
Stage 1 Discovery
One Stage
1 cycle is
limited to 5
seconds
HTTP Get to Discovery Host (IF available)
HTTP Get to enroll.cisco.com
HTTP Get to Default GW IP
HTTPS request to PSN
Find My Session {IP Array}, {MAC Array},
Session
lookup in
Local PSN
cache
(IP/MAC
based)
Session
lookup on
MNT cache
(MAC only)
ISE
PSN
ConnectionData.xml
BRKSEC-3077
114

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
PSN discovery Non-redirect based flow
Network Access Device
Stage 2 Discovery
Stage 2
probes
executed
sequentially
URL
/auth/ng-
discovery
HTTPS request to Call Home Address
HTTPS request to PSN
HTTPS request to enroll.cisco.com
Find My Session {IP Array}, {MAC Array},
ISE
PSN
Find My Session {IP Array}, {MAC Array},
Find My Session {IP Array}, {MAC Array},
BRKSEC-3077
115

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
PSN discovery Non-redirect based flow
Network Access Device
Stage 2 Discovery
Stage 2
probes
executed
sequentially
URL
/auth/ng-
discovery
HTTPS request to Call Home Address
HTTPS request to PSN
HTTPS request to enroll.cisco.com
Find My Session {IP Array}, {MAC Array},
ISE
PSN
Find My Session {IP Array}, {MAC Array},
Find My Session {IP Array}, {MAC Array},
BRKSEC-3077
116

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
PSN discovery Non-redirect based flow
Network Access Device
Stage 2 Discovery
Stage 2
probes
executed
sequentially
URL
/auth/ng-
discovery
HTTPS request to Call Home Address
HTTPS request to PSN
HTTPS request to enroll.cisco.com
Find My Session {IP Array}, {MAC Array},
ISE
PSN
Find My Session {IP Array}, {MAC Array},
Find My Session {IP Array}, {MAC Array},
BRKSEC-3077
117

Misconception
n. 3: Compliant
State ISE vs
Secure Client

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
AnyConnect Compliant State
“Secure Client is aware of its Compliant State on ISE”
BRKSEC-3077
119

Secure Client is aware of
its Compliant State on ISE
ⓘ Start presenting to display the poll results on this slide.

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
The problematic scenario
ISE
L2 Change
Posture Status = Posture Pending
BRKSEC-3077
121

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Bidirectional Posture
BRKSEC-3077
Secure Client/AnyConnect will probe ISE if in Compliant state
ISE
Port 8449
Or
Anyconnect 4.10+
ISE 3.1+
122

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Bidirectional Posture – Correct Implementation
BRKSEC-3077
ISE
Compliant
ISE
Pending
DACL deny PSN port 8449
DACL permit PSN port 8449
126

Demo – Bidirectional
Posture Configuration

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Insert Bidirectional Posture Demo

Advanced ISE
Posture
Deployments –
Use Cases

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
1. Posture over VPN with ASA or
FTD when DUO proxy is used
2. Posture over VPN with ASA
configured for SAML
authentication on DUO Access
Gateway (DAG)
3. Posture on dot1x media with
DUO proxy
Posture and MFA
Possible scenarios:
BRKSEC-3077
131

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Posture and MFA – VPN with DUO proxy (flow)
ISE
VPN Authentication
Radius
Access-Request
LDAP
authentication
Request for second factor
DUO Push
Radius
Access-Accept
Allow Access
Radius
Access-Accept
Accept
BRKSEC-3077
133

Demo – ISE
Configuration

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ASA Configured for SAML with SSO
BRKSEC-3077
ISE
1
2
3
4
5
8
6
7
10
9
11
138

Demo

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public

ISE Posture
troubleshoot
deep dive

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Posture Troubleshooting Journey
Define the Problem
Agent Side
Troubleshooting
NAD
Troubleshooting
Confirm the theory
3
rd
Party Troubleshooting
Build the
theory
ISE Troubleshooting
BRKSEC-3077
143

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Status of the authentication session at
time of the issue
Device configuration
Debugs for Authentication/Accounting
and Redirect activities
DART bundle collected after the
problem
Screenshots/Recording of user
experience
Packet capture collected when issue
manifested
Exact Timestamp
System Scan Details from
AnyConnect
Live Logs/Detailed authentication
reports for affected endpoint
Client Provisioning Report filtered by
endpoint MAC
Posture Report filtered by endpoint
MAC
Radius Authentication/Accounting
reports for the affected endpoint
Support bundle with posture related
components in ’DEBUG’
Screenshots of related ISE
configuration
Packet capture collected when issue
manifested
Most commonly
needed
Less commonly needed
ISE
Posture troubleshooting, what to collect
BRKSEC-3077
146

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Learn on Example
BRKSEC-3077
No Policy Server Detected
147

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Learn on Example – Failed to launch Downloader
BRKSEC-3077
148

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Insert Problematic Scenario Demo

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Define the Problem
BRKSEC-3077
ISE Posture Agent is now failing with Failed to Launch Downloader
150

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Define the Problem
BRKSEC-3077
ISE Posture Agent is now failing
with Failed to Launch Downloader
Which is the problematic pillar ?
151

Agent Side
Troubleshooting
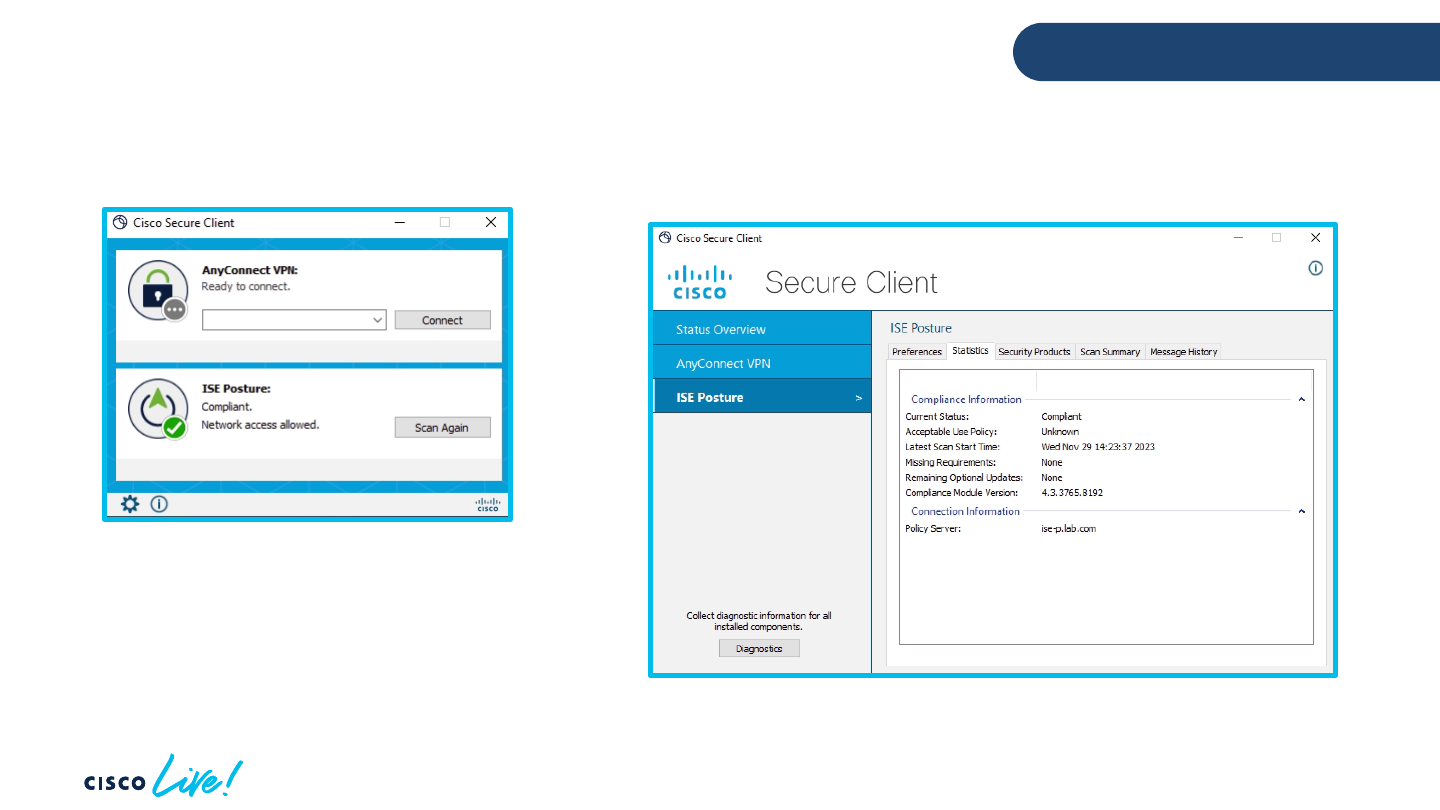
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
System Scan Details
BRKSEC-3077
Agent Troubleshooting
153

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Posture - Details
BRKSEC-3077
Time and data of last scan
Current posture status
returned from ISE to endpoint
FQDN of the PSN which performed
last posture check
Agent Troubleshooting
154

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Posture - Security Products
BRKSEC-3077
Names of the detected security
products
Product types like AM (Anti-Malware),
PM (Patch Management)
FW (Firewall)
Version of installed security products
Definition versions and definition
dates (if applicable)
Agent Troubleshooting
155

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ISE Posture – Scan Summary
BRKSEC-3077
Status for each Requirement
obtained from PSN (Passed/Failed)
List of the Requirement obtained
from ISE. Requirements names here
are the same which defined on ISE.
Agent Troubleshooting
156

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Clearing Logs
BRKSEC-3077
Agent Troubleshooting
158

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Packet Capture
BRKSEC-3077
http DNS IP address of PSNs
For general redirect
troubleshooting
tcp.port==80 is more effective
In case if we know which FQDN
we are looking for:
dns.qry.name ==
"posture.demo.local
In unknown environment better
to use CP portal port as a filet:
tcp.port==8443
Agent Troubleshooting
159

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
1. Find Discovery Restart event closest to the issue timestamp (keywords ‘Restarting
Discovery’, ‘HTTP Discovery’),
1. Highlight every stage 1 probe target (Keyword ‘Probing no MNT stage targets’),
2. Follow the logs to see result for each probe
Agent side troubleshooting – DART analysis
2024/01/16 02:05:15 [Information] csc_iseagent Function:
SwiftHttpRunner::collectNoMntTargets Thread Id: 0x1070 File: SwiftHttpRunner.cpp Line: 1400
Level: debug
Probing no MNT stage targets (#5): Redirection target 10.52.14.254, Redirection target
fe80::5:73ff:fea0:e, Redirection target enroll.cisco.com,
Auth-Status target ise-p.lab.com with path /auth/status, Auth-Status target ise-s.lab.com with
path /auth/status, .
2024/01/16 02:05:17 [Information] csc_iseagent Function: Target::Probe Thread Id: 0x1140 File: Target.cpp
Line: 212 Level: debug Status of Redirection target 10.52.14.254 is 6 <Not Reachable.>.
Agent Troubleshooting
BRKSEC-3077
167

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
4. Find which PSN in the deployment replied to the agent
5. Make a note of the session ID from reply
DART analysis
Agent Troubleshooting
BRKSEC-3077
169

Demo – Learn on the
example

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Agent Troubleshooting 1

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public

Network Device
Troubleshooting

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Cisco Switch
BRKSEC-3077
ISE
Pending
• Show access-session
• IP Device Tracking DB
NAD Troubleshooting
175

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Cisco Switch
BRKSEC-3077
NAD Troubleshooting
176

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Cisco Switch - Access Session Details
BRKSEC-3077
NAD Troubleshooting
177

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Cisco Switch – Device Tracking
BRKSEC-3077
NAD Troubleshooting
178

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
HTTP Server
BRKSEC-3077
Http server on the switch disabled by default and need to be enabled by
typing:
(config)#ip http server
Often customers are against enabling http server since it may make switch
vulnerable.
To keep only web redirect functionality and disable everything else we
use:
(config)#ip http active-session-modules none
NAD Troubleshooting
179

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
ASA/FTD
BRKSEC-3077
What is different
1. Not all traffic may go into tunnel (tunnel–all VS split-tunneling)
2. MAC OS has no default GW on VPN adapters (utunX)
3. ASA can push AnyConnect posture resources to client (ISE posture
module, ISE posture profile but not a compliance module)
Cisco Secure
Firewall
NAD Troubleshooting
186

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Cisco ASA/FTD - Resources
BRKSEC-3077
Ideally same AC version should be installed on both ASA/FTD and ISE
It’s possible to enable ‘defer update’ settings in ISE AC config but if user
will press update accidently this will result in error
If ISE > ASA
ASA > ISE
ASA = ISE
NAD Troubleshooting
187

Troubleshooting
ISE

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Troubleshooting ISE
BRKSEC-3077
Detailed Authentication report is always a good starting point
Live Logs
ISE Troubleshooting
190

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Troubleshooting ISE
BRKSEC-3077
Detailed Authentication report is always a good starting point
Take a note of authorization
policy and authorization profile
name. This may be needed for
further configuration validation
ISE Troubleshooting
191

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Troubleshooting ISE
BRKSEC-3077
Write down name of the PSN
which performed authentication
ISE Troubleshooting
192

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Troubleshooting ISE
BRKSEC-3077
Redirect attributes returned to
NAD
ISE Troubleshooting
193

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Posture Assessment Report
BRKSEC-3077
ISE Troubleshooting
194

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Posture Assessment Report
BRKSEC-3077
Take a note of last
posture scan time
Check what decision ISE made
(Compliant/Non-Compliant)
Open detailed report to
gather more data
ISE Troubleshooting
195

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Posture Assessment Report
BRKSEC-3077
List of matched
posture Policies
Posture requirements
taken from Posture
Policies
Type of the
requirement
Result of
posture check
Names of
passed posture
conditions
ISE Troubleshooting
196

Learn on
Example

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Troubleshooting ISE

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Where we are
BRKSEC-3077
• Captures shows no
communication over port
8443
• Packets are not crossing the
switch
• Pending state on ISE, no
posture Reports received
Learn on Example
199

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Third party Firewall
BRKSEC-3077
Local team added on Secure Endpoint more restrictive rules due to a
missing fix on a specifiv CVE.
This was breaking the communications over port 8443 to ISE
TCP.PORT 8443
Learn on Example
200

Wrap up time

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Define the problem
Understand how it
should work
Decide what to
collect and collect
the data
Analyze the data to
build the theory
Confirm the theory
Key Takeaways
BRKSEC-3077
221

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Work on the different ISE Pillars
Advanced Scenarios are just bigger puzzles
Posture is only part of the
puzzle
Understand exactly the flow
and where posture is going
to fit
01 02 03 04
Key Takeaways Posture Deployment
BRKSEC-3077
222

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco PublicBRKSEC-3077
Security
ISE
Learn how Cisco ISE will help you implement
Network access Control in your campus. Sessions
will cover how to plan and deploy, how to leverage
the new cloud capabilities, best practices and
other topics.
Monday, February 5 | 8:45 a.m.
START
TECSEC-3416
Walking on Solid ISE: Advanced
use cases and deployment best
practices
Monday, February 5 | 2:15 p.m.
TECSEC-3503
Segmenting industrial networks
with Trustsec and Cisco Identity
Services Engine
Tuesday, February 6 | 8:00 a.m.
BRKSEC-2889
Mastering ISE Upgrades: Best
Practices, Tips, and Tricks
Tuesday, February 6 | 5:00 p.m.
BRKSEC-2660
ISE Deployment Staging and
Planning
Wednesday, February 7 | 10:30
a.m.
BRKSEC-2039
Secure Access with ISE in the
Cloud
Thursday, February 8 | 8:45 a.m.
BRKSEC-2100
ISE Your Meraki Network with
Group Based Adaptive Policy
Thursday, February 8 | 2:30 p.m.
BRKSEC-3077
A song of ISE and Posture:
Advanced deployment and
troubleshooting
Thursday, February 8 | 4:30 p.m.
BRKSEC-2234
Cisco ISE Performance, Scalability
and Best Practices
Friday, February 9 | 9:15 a.m.
FINISH
BRKSEC-3412
Unleashing the Art of
Troubleshooting Authenticaton
Latency issues.
If you are unable to attend a live session, you can watch it in the On-Demand Library after the event.
223

Thank youThank you

