
Blue Coat ProxySG First Steps
Solution for Controlling Web Applications
SGOS 6.7

Legal Notice
Copyright © 2018 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and
the Blue Coat logo are trademarks or registered trademarks of Symantec Corp. or its affiliates in the U.S. and other countries.
Other names may be trademarks of their respective owners. This document is provided for informational purposes only and is
not intended as advertising. All warranties relating to the information in this document, either express or implied, are
disclaimed to the maximum extent allowed by law. The information in this document is subject to change without notice.
THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS,
REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT
THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE
LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING,
PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS
DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. SYMANTEC CORPORATION PRODUCTS,
TECHNICAL SERVICES, AND ANY OTHER TECHNICAL DATA REFERENCED IN THIS DOCUMENT ARE SUBJECT
TO U.S. EXPORT CONTROL AND SANCTIONS LAWS, REGULATIONS AND REQUIREMENTS, AND MAY BE
SUBJECT TO EXPORT OR IMPORT REGULATIONS IN OTHER COUNTRIES. YOU AGREE TO COMPLY STRICTLY
WITH THESE LAWS, REGULATIONS AND REQUIREMENTS, AND ACKNOWLEDGE THAT YOU HAVE THE
RESPONSIBILITY TO OBTAIN ANY LICENSES, PERMITS OR OTHER APPROVALS THAT MAY BE REQUIRED IN
ORDER TO EXPORT, RE-EXPORT, TRANSFER IN COUNTRY OR IMPORT AFTER DELIVERY TO YOU.
Symantec Corporation
350 Ellis Street
Mountain View, CA 94043
www.symantec.com
3/20/2018

Blue Coat ProxySG First Steps
Contents
Solution:Control Web Applications 4
Set Web Services to Intercept 4
Select a Content Filtering Provider 4
Determine Which Web Applications to Control 8
Create Policy to Control Web Applications 10
Example: Control YouTube Operations 10
Test Web Application Policy 13
View the Application Mix Report 14
Web Application Troubleshooting 16
Why aren't web apps being blocked? 16
How does the ProxySG categorize the application and operation for a user transaction? 16
Is the web app policy being applied? 17
3

Controlling Web Applications
Solution:Control Web Applications
In addition to URL category filtering, you can filter content by web application and/or specific operations or actions done
within those applications. Starting in SGOS 6.7.2, you can also filter content by web application group.
Here are several examples of how you can use web application controls in policy:
n Block access to web applications in the Gamification Platform group.
n Allow users to access all social networking sites, except for Facebook. Conversely, block access to all social
networking sites except for LinkedIn.
n Allow users to post comments and chat in Facebook, but block uploading of pictures and videos.
n Prevent the uploading of videos to YouTube, but allow all other YouTube operations such as viewing videos others
have posted. Conversely, prevent uploading but block access to some videos according to the video’s category.
n Allow users to access their personal email accounts on Outlook.com, AOL Mail, and Yahoo Mail, but prevent them
from sending email attachments.
Steps
1. Set web services to intercept, such as External HTTP and HTTPS. See "Set Web Services to Intercept" below.
2. Select the content filtering provider for which you have a subscription. See "Select a Content Filtering Provider"
below.
3. Decide which web applications, groups, and operations you want to control. See "Determine Which Web
Applications to Control" on page8.
4. "Create Policy to Control Web Applications" on page10.
5. "Test Web Application Policy" on page13.
6. "View the Application Mix Report" on page14.
Set Web Services to Intercept
Make sure web services, such as External HTTP (transparent port 80) and HTTPS (transparent port 443), are set to
intercept, or if your proxy is deployed explicitly, ensure that the Explicit HTTPservice has Detect Protocol enabled.
Select a Content Filtering Provider
The ProxySG uses the content filtering feature to identify web applications based on URLs. Symantec offers several
content filtering databases:
n Blue Coat WebFilter: the legacy on-box content filtering database (not covered in this solution)
n Intelligence Services (Standard): a subscription to an enhanced on-box content filtering database with basic web
application controls
n Intelligence Services (Advanced):in addition to features of the standard subscription, includes threat risk and
geolocation controls
4

Blue Coat ProxySG First Steps
To control access to web applications, you need to enable the Blue Coat content filtering provider, select the data source
(WebFilter or Intelligence Services), enable Application Classification, and download the latest database.
1. Confirm that you have a Proxy Edition license (not a MACH5 license). The license name appears in the
Management Console banner.
2. Confirm the ProxySG has a valid content filtering subscription:
a. Select Maintenance > Licensing.
b. In SGOS 6.7.4 or higher: Click the Subscription tab.
In earlier versions: Click the View tab.
c. Look for one of the following:
Advanced Web Security and Basic Web Applications
Standard Web Security and Basic Web Applications
d. Locate the expiration date for the subscription and make sure Basic Web Application Controls is listed
under Data feeds. Show example...
3. Enable the Blue Coat content filtering provider:
a. Select Configuration > Content Filtering > General.
b. For Blue Coat, select the check box in the Enable column.
5

Controlling Web Applications
c. Click Apply.
4. Select the data source that corresponds to your subscription (WebFilter or Intelligence Services):
a. Select Configuration > Content Filtering > Blue Coat.
b. For Data Source, select Intelligence Services.
c. Click Apply.
6

Blue Coat ProxySG First Steps
5. Download the current content filtering database.
a. In the Blue Coat tab (Configuration > Content Filtering > Blue Coat), click Download Now.
6. Enable Application Classification.
a. Select Configuration > Application Classification > General.
b. Enable the check box Enable Blue Coat Application Classification on this device.
c. Click Apply.
7.
Intelligence Services only:
Download the current application database (not applicable to WebFilter data source).
a. On the Application Classification General page, click the Download tab.
b. Click Download Now.
7

Controlling Web Applications
Determine Which Web Applications to Control
Before creating policy to control web applications, you may want to do some investigation into what applications and
groups are available, or what application and group is associated with a particular URL. You can then use these
specifications when creating web application policy.
8

Blue Coat ProxySG First Steps
1. Select Configuration > Application Classification > General > General.
2. Click the following links to view lists of supported applications, groups, and operations:
View Application List
View Operation List
View Group List
3. To find the application, operation, and group associated with a URL, enter a URL in the URL field and click
Lookup.
The console displays the lookup results.
4. For a list of supported web applications, see http://sitereview.bluecoat.com/applications.jsp.
9

Controlling Web Applications
Please note that operations may not include the full details of operations per platform (for example, a web
application may support post messages and send email on Desktop Browser, but on the iOS platform, it could be
just allow/deny).
Create Policy to Control Web Applications
To allow and deny access to web applications, groups, and operations, you create policy rules in the Web Access Layer.
1. Launch the Visual Policy Manager (VPM).
a. In the Management Console, select Configuration > Policy > Visual Policy Manager.
b. Click Launch.
2. Add a Web Access Layer.
a. Select Policy > Add Web Access Layer.
b. For Layer Name, enter a descriptive name and click OK.
3. Right-click the Destination column within the rule, and select Set.
4. To control web applications, click New and select Application Name. In the new window that opens, select the
check box of the application(s) you want to control and click OK.
You can use the Name filtering field to quickly find an application.
Alternatively, you can select Application Group to control all web applications in a particular group.
5. (Optional) To control web operations:
a. Click New and select Application Operation.
b. In the Supporting application list, select the web application(s) you want to control.
c. Select the check box of the operation(s) you want to control.
d. Click OK.
6. Click OK again to close the object dialog.
7. Set Action to Allow or Deny, depending on the policy you want to create.
8. Click Install policy.
Example: Control YouTube Operations
Next Step: "Test Web Application Policy" on page13
Example: Control YouTube Operations
The following example demonstrates how to add a policy to control YouTube operations. With this policy, users will not be
able to post messages or upload videos in the YouTube application; all other operations will be allowed.
10
Blue Coat ProxySG First Steps
1. Launch the VPM.
2. Add a Web Access Layer. Name the layer
YouTube Controls
.
3. Right-click the Destination column within the rule, and select Set.
4. Click New and select Application Name.
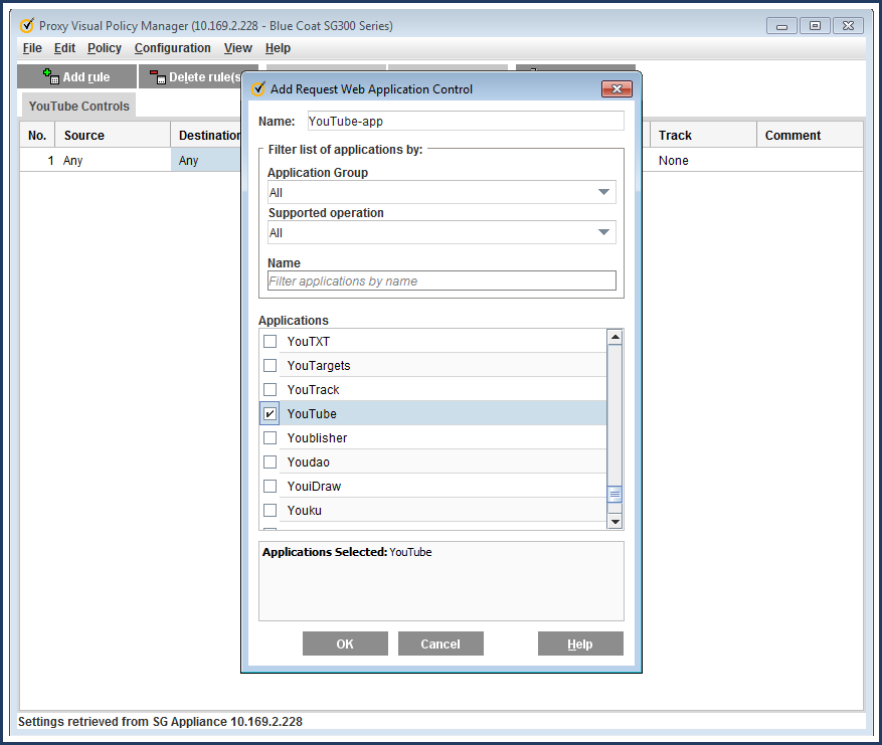
5. In the application list, scroll down and select the YouTube check box.
6. In the Name field, enter a descriptive name such as
YouTube-App
, click OK.
7. Add an object to deny Post Messages and Upload Videos operations on YouTube.
a. Click New and select Application Operation.
b. Under the Supporting application list, select YouTube.
c. Select the operations you want to block: Upload Videos and Post Messages.
d. Name this object
YouTube-Operations
.
e. Click OK.
8. Create a combined object.
a. Click New and select Combined Destination Object.
b. Add
YouTube-App
to the upper-right box and add and
YouTube-Operations
to the lower-right box. This
ensures that both conditions must match for this policy to deny requests.
11

Controlling Web Applications
c. Name the combined object
YouTube app-op controls
. Click OK.
9. Click OK again to close the object dialog.
10. Make sure the Action is set to Deny.
11. Install the policy.
You can verify the full policy details on the ProxySG. In the VPM, click View > Current SG Appliance VPM Policy Files.
If you have multiple access layers in the VPM, you can see the order in which the rules will be applied in the CPL
(content policy language) file. On the VPM, go to View > Generated CPL.
12

Blue Coat ProxySG First Steps
Test Web Application Policy
Test the policy by verifying that you cannot access blocked web applications.
1. Open a web browser that is configured to use the ProxySG as proxy. Make sure that you are not using the same
browser that you are currently using to access the Management Console.
2. Launch the application that you created policy for. For example, if you created policy to deny Facebook access,
you will see a corresponding ‘access denied’ or ‘web page not found’ error depending on how you have configured
the Deny functionality.
13

Controlling Web Applications
3. If you created policy to block web applications in a particular group, try launching a variety of applications in that
group; if the policy is working properly, you should be denied access to each application.
4. To customize the web page containing the error message displayed to users when they are denied access to a
URL, refer to the Exception Pages solution in the First Steps WebGuide.
Verify that you cannot perform blocked web operations and can perform operations that are allowed.
1. Open a web browser that is configured to use the ProxySG as proxy.
2. Launch the application you created policy for. Make sure you can perform operations that are allowed and are
denied access to the blocked operations. For example, if you created policy to block Post Messages and Upload
Videos operations in YouTube, go to YouTube and try to upload a file or post a comment; these operations should
be denied. Other operations, such as playing videos, should be allowed.
View the Application Mix Report
The Application Mix report shows a breakdown of the web applications running on the network. This report can give you
visibility into which web applications users are accessing, the amount of bandwidth these applications are consuming,
and how much bandwidth is gained by optimization of web applications over different time periods.
1. Select Statistics > Application Details > Application Mix.
2. Select a time period from the Duration drop-down list.
14
Blue Coat ProxySG First Steps
The pie chart displays data for the seven applications with the most traffic during the selected time period. If there
are more than seven applications classified during that time, the applications with the least amount of traffic are
combined into an Other slice. The <Unidentified> slice includes traffic for which the URL is not a web application,
or is a web application that is not currently supported in the database. <Unidentified> also includes web traffic for
applications that could not be identified because there was a problem with the WebFilter or Intelligence Services
subscription or database.
15

Controlling Web Applications
Web Application Troubleshooting
Why aren't web apps being blocked? 16
How does the ProxySG categorize the application and operation for a user transaction? 16
Is the web app policy being applied? 17
Why aren't web apps being blocked?
Problem: The policy that is supposed to block web applications or operations is not denying access to the objects defined
in the policy.
Resolution: If the application, group, or operation you have set a policy for is not getting blocked, try the following:
n Make sure your browser has been configured to use the proxy with the correct port and proxy IP address.
n Make sure that your ProxySG is intercepting HTTP/HTTPS traffic. See "Set Web Services to Intercept" on page4.
n Make sure the policy is correctly installed
1. Click Configuration > Policy > Policy Files.
2. Under View Policy, select Current Policy and click View.
n Check to see if your traffic is passing through the proxy by temporarily denying all traffic to a test user client IP.
1. Open the Visual Policy Manager.
2. Select Policy > Add Web Access Layer. Type a layer name (such as Test) and click OK. This new Web
Access layer will have just one rule in it.
3. In the Source column, right-click and select Set > New. Select Client IP address/Subnet.
4. Enter the IP address of the client you are running the testing from. There is no need to enter a subnet.
5. Select Add > Close. In the Set Source Object window, select this client IP and then OK.
6. Right-click the Action column, and select Set. From the list of existing objects, choose Force Deny and
click OK.
7. From the test machine (the client IP you created policy for), open a new tab in the browser and go to any
website. You should be blocked unless you have added an ‘allow policy exception’ for that particular
website in your VPM.
8. When you are done testing, remove the layer you added above.
n You can also view a trace to see if the policy is being applied. See "Is the web app policy being applied?" on the
next page.
How does the ProxySG categorize the application and
operation for a user transaction?
Problem: When troubleshooting web application policy, it's helpful to see how the ProxySG is categorizing the application
and operation for a user transaction.
Resolution: A policy trace includes an indication of the application name and operation for a particular URL or request. To
create a policy trace that only captures the transactions or traffic coming from a specific IP address:
16
Blue Coat ProxySG First Steps
1. Open the Visual Policy Manager.
2. Select Policy > Add Web Access Layer. Type a layer name and click OK. This new Web Access layer will have
just one rule in it.
3. In the Source column, right-click and select Set > New. Select Client IP address/Subnet.
4. Enter the IP address of the client you are running the testing from. There is no need to enter a subnet.
5. Select Add > Close. In the Set Source Object window, select this client IP and then OK.
6. Change the Action to None. Right-click on Allow action and choose Delete.
7. In the Track column, right-click on None, select Set > New > Trace.
8. Click the Trace Level check box and the Enable trace radio button. Click OK.
9. Install the policy.
10. Open a browser to the following URL: https://Proxy SG IP address:8082/Policy/Trace/default_
trace.html
In the policy trace, there will be an indication of the application name and operation for that particular URL or request.
Below is an example that shows a POST request that was made when a user sent an email from Gmail.
POST http://mail.google.com/mail/...
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:23.0) Gecko/20100101 Firefox/23.0
user: unauthenticated
url.category: Email@Blue Coat
application.name: Gmail
application.operation: Send Email
DSCP client outbound: 65
DSCP server outbound: 65
stop transaction --------------------
Sometimes, multiple transactions can be seen even though you have specified only one IP because a web page can make
an HTTP or HTTPS request in the background without a user knowing it. Therefore, you would need to be sure that the
URL in the policy trace is the request that you made when you make an action such as clicking the Send button in Gmail.
Is the web app policy being applied?
To see if a web application policy is being applied, you can view a policy trace.
1. Open the Visual Policy Manager.
2. Select Policy > Add Web Access Layer. Type a layer name and click OK. This new Web Access layer will have
just one rule in it.
3. In the Source column, right-click and select Set > New. Select Client IP address/Subnet.
4. Enter the IP address of the client you are running the testing from. There is no need to enter a subnet.
5. Select Add > Close. In the Set Source Object window, select this client IP and then OK.
6. Change the Action to None. Right-click on Allow action and choose Delete.
7. In the Track column, right-click on None, select Set > New > Trace.
8. Click the Trace Level check box and the Trace enabled radio button. Click OK.
9. Install the policy.
10. Open a browser to the following URL: https://Proxy SG IP address:8082/Policy/Trace/default_
trace.html
17

Controlling Web Applications
11. Open a new browser that is configured to use the proxy. Go to YouTube (assuming you added a policy for YouTube
earlier), and try to access YouTube or perform an operation in YouTube such as ‘upload video.’ As you do this, you
will see a live trace of this traffic on the Default Trace page that you had open.
12. If the policy is being applied correctly, you will see that the policy matches some of the URLs and the traffic was
denied as shown in the screenshots below.
Examples
Access Denied
18

Blue Coat ProxySG First Steps
Default Trace
19
